
Your SOC is drowning in alerts. Your compliance team spends more time collecting evidence than analyzing it. Your observability data lives in a different tool than your security logs. And every vendor wants you to rip out what you have and start over.
Agentic Log Management is a different approach—one that treats logs as a foundation for autonomous investigation, not just storage. Instead of passive dashboards, you get AI agents that ingest, interrogate, and act on logs across security, compliance, observability, and FinOps.
No hallucinations—answers grounded in your data. Outcome-driven, not storage-driven.
Agentic Log Management represents a paradigm shift from passive log collection to active, autonomous orchestration. Instead of relying on static dashboards or siloed tools (like SIEM, observability platforms, or data lakes), agentic systems deploy specialized AI agents that continuously monitor, investigate, and respond to log-derived events in real-time.
These agents are trained on your organization's unique systems and data structures, enabling dynamic collaboration between bots—with memory, autonomy, and built-in security knowledge—to deliver faster, more reliable outcomes across your entire tech stack.
Key Traits:
Security and IT teams have been managing logs for decades. The tools have evolved—from syslog servers to SIEMs to cloud-native observability platforms—but the fundamental challenges have compounded rather than resolved.
Fragmentation: Juggling SIEMs, observability tools, and compliance dashboards leads to redundant ingestion and manual correlation. Your security data lives in one place, your application performance data in another, your compliance evidence in a third.
Cost Pressure: Legacy vendors charge by volume and storage—not outcomes. Teams pay for logs they never use, and cost constraints force difficult tradeoffs between visibility and budget.
Staffing Gaps: Ops teams are buried under alerts and disconnected workflows. Scaling headcount isn't feasible, and even if it were, you can't hire your way out of a 3,800-alerts-per-day problem.
Slow Response: Incidents queue up for hours. Manual playbooks are brittle and blind to context. By the time an analyst investigates, attackers have moved on.
The AI Opportunity: Agentic AI shifts the model: from dashboards to doers, from manual response to autonomous copilots. Logs become a strategic advantage rather than compliance overhead.
Agentic Log Management doesn't just collect data—it understands it. By combining intelligent AI agents with your real-time data, you move from reactive investigation to proactive resilience.
The transformation happens in stages. Every data source gets unified into a knowledge graph, mapping relationships across users, systems, and events. Analysts ask questions in plain language—AI interprets intent and highlights anomalies in real time. Context-rich alerts explain why events matter, turning noise into guided decision points. Repeated decisions get automated through SOAR playbooks, enforcing compliance and audit readiness. And leaders gain continuous insight into detection speed, risk posture, and analyst productivity.
Result: Log management transforms from an archival necessity into an adaptive intelligence engine—enabling security teams to predict, prioritize, and act at the speed of threat.
From collecting and visualizing logs to orchestrating outcomes with specialized AI agents. Here's how agentic teams compare to SIEM, Observability/APM, Data Lakes, and SOAR.
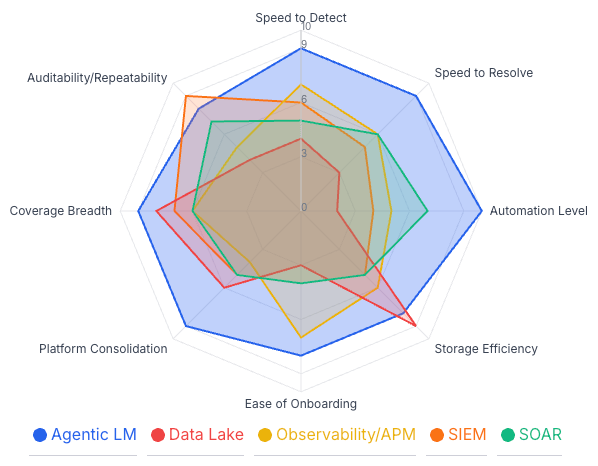
Agentic Log Management replaces siloed tools with a collaborative team of purpose-built AI agents that monitor, investigate, and remediate across your stack.
Early deployments show 60–80% reduction in mean time to resolve and 30–50% increased coverage from cross-domain correlation.
Watch an agent investigate a real alert across your actual log sources—no migration required, no rip-and-replace. Schedule a demo with Strike48 to see more.